Session Monitoring
Monitor and verify access continuously throughout user sessions. Advanced behavioral analysis and real-time threat detection with adaptive security policies.
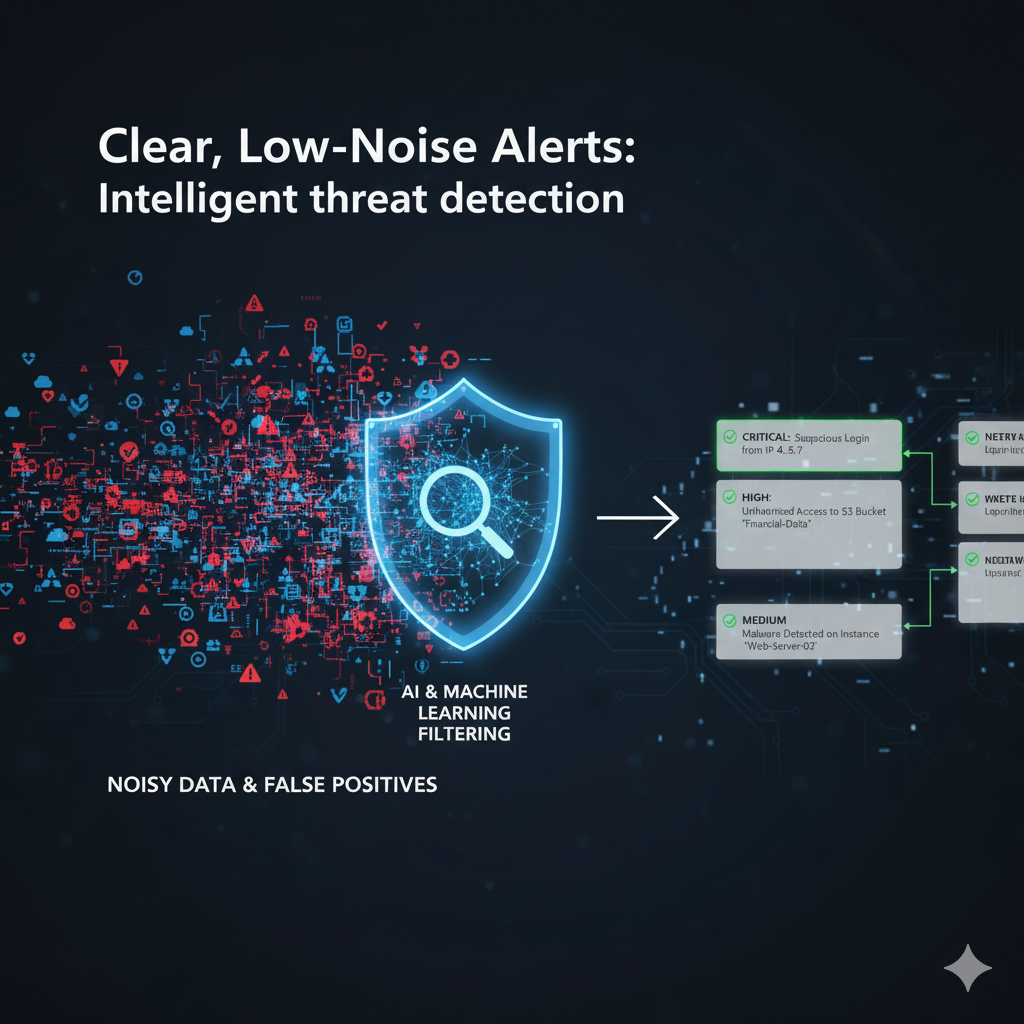
Continuous Verification Features
Advanced session monitoring with intelligent behavioral analysis and real-time anomaly detection capabilities
Session Monitoring
Real-time tracking of user activities, access patterns, and session behaviors across all applications.
Behavioral Analysis
Machine learning algorithms analyze user behavior patterns to establish baselines and detect anomalies.
Anomaly Detection
Intelligent detection of unusual activities, impossible travel, and suspicious access patterns.
Real-time Alerts
Instant notifications for security events with automated response triggers and escalation workflows.
Adaptive Policies
Dynamic security policies that adjust based on risk levels, context, and user behavior patterns.
Session Lifecycle
Complete session management with timeout controls, re-authentication triggers, and access revocation.
Continuous Verification Process
Establish user behavioral baselines during normal operations
Monitor session activities and access patterns in real-time
Detect anomalies using machine learning and risk scoring
Trigger adaptive responses and re-authentication as needed
Ready for Continuous Verification?
Start securing your organization with advanced session monitoring and behavioral analysis today.