Infrastructure as Code Security
Secure your Infrastructure as Code with automated CloudFormation template analysis, drift detection, and compliance validation for enterprise DevSecOps.
Why Infrastructure as Code Security Matters
Infrastructure as Code (IaC) accelerates deployment but can also propagate security misconfigurations across your entire cloud environment. A single insecure template can create hundcyans of vulnerable resources.
Securitain provides comprehensive CloudFormation security scanning that catches vulnerabilities before deployment and continuously monitors for configuration drift and compliance violations in your live infrastructure.
Comprehensive IaC Security Features
End-to-end security for your Infrastructure as Code lifecycle
Comprehensive scanning of CloudFormation templates for security misconfigurations, over-permissive policies, and compliance violations before deployment.

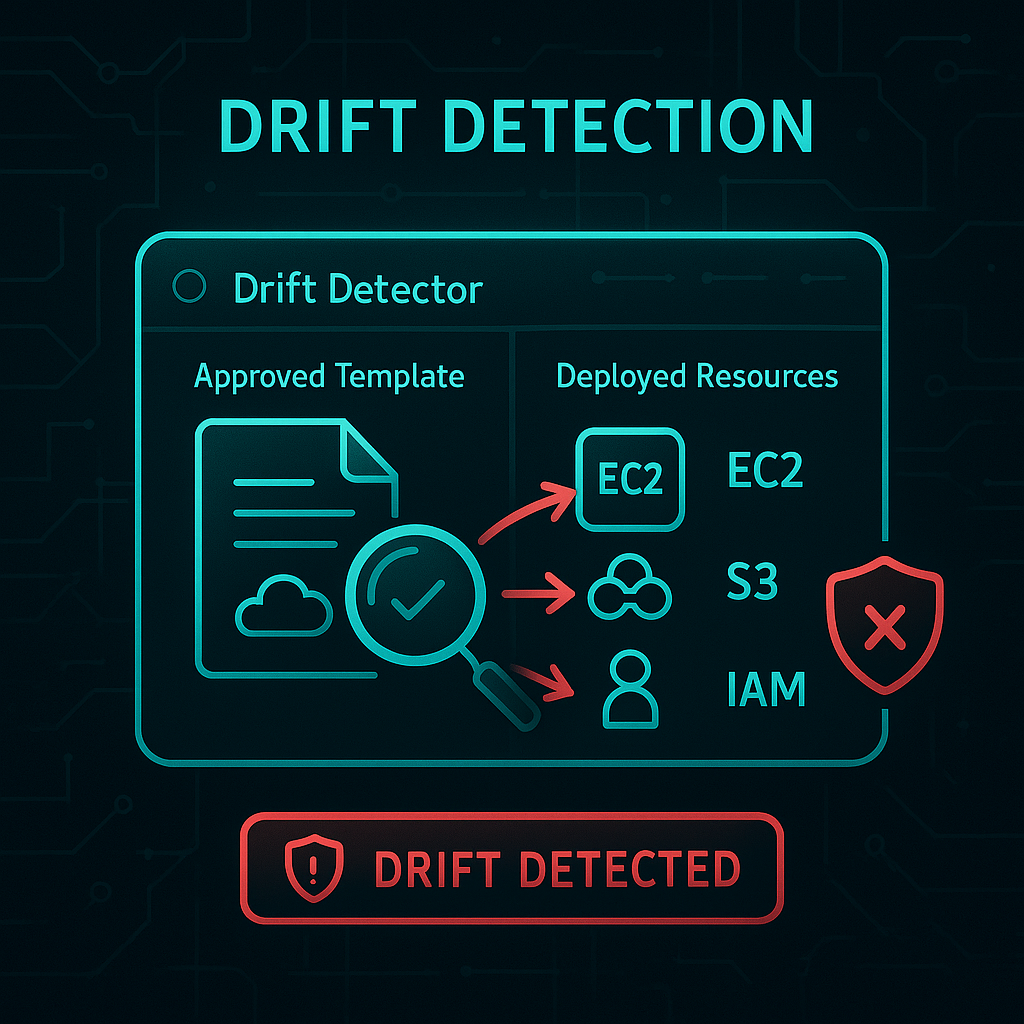
Continuous monitoring of deployed infrastructure to detect configuration drift and unauthorized changes from your approved CloudFormation templates.
Automated validation against industry standards including CIS benchmarks, NIST frameworks, and custom organizational policies.

Seamless integration with CI/CD pipelines for automated security scanning and policy enforcement during the development lifecycle.

Comprehensive Security Checks
IAM roles and policies for least-privilege access
S3 bucket security configurations and public access
VPC security groups and network access controls
Encryption settings for data at rest and in transit
Resource-level security configurations
Cross-service permissions and trust relationships
DevSecOps Integration
Seamlessly integrate security into your development workflow
Pre-Deployment Scanning
Scan CloudFormation templates in your development environment before deployment to catch security issues early.
CI/CD Pipeline Integration
Native integration with Jenkins, GitHub Actions, GitLab CI, and other CI/CD platforms for automated security checks.
Policy as Code
Define and enforce security policies as code, enabling version control and collaborative policy management.
Automated Remediation
Generate compliant CloudFormation templates and provide step-by-step remediation guidance for security issues.
Compliance Framework Support
Automated compliance validation against industry standards and regulations
CIS AWS Foundations Benchmark
Automated compliance checking against CIS security best practices
NIST Cybersecurity Framework
Infrastructure alignment with NIST security controls and guidelines
SOC 2 Type II
Security controls validation for service organization compliance
PCI DSS
Payment card industry security standards for infrastructure components
HIPAA
Healthcare compliance requirements for AWS infrastructure
FedRAMP
Federal risk management program compliance for government workloads
Infrastructure as Code Best Practices
Implement least-privilege IAM policies and roles
Enable comprehensive logging and monitoring across all resources
Enforce encryption for data at rest and in transit
Configure secure network architectures with proper segmentation
Implement resource tagging for security and compliance tracking
Use AWS Secrets Manager for sensitive configuration data
Enable AWS Config for continuous compliance monitoring
Implement backup and disaster recovery configurations
Automated Remediation Capabilities
Automated generation of secure CloudFormation templates
Step-by-step remediation guides with code examples
Integration with AWS Config for automated remediation
Custom remediation scripts for common security issues
Bulk remediation capabilities for multiple resources
Rollback capabilities for safe configuration changes
CloudFormation Template Analysis in Action

Real-Time Security Analysis
See how our platform identifies security vulnerabilities and compliance issues in CloudFormation templates with detailed remediation guidance.
Secure Your Infrastructure as Code Today
Start scanning your CloudFormation templates for security vulnerabilities and compliance issues. Integrate security into your DevSecOps pipeline from day one.