Zero-Trust Components
Comprehensive security architecture for modern cloud environments
Identity-Based Access
Verify user identity through multi-factor authentication and behavioral analysis.
MFA enforcement →
Get Started with SecuritainDevice Trust
Ensure device compliance and security posture before allowing access.

Device registration →
Get Started with SecuritainContinuous Verification
Monitor and verify access continuously throughout user sessions.
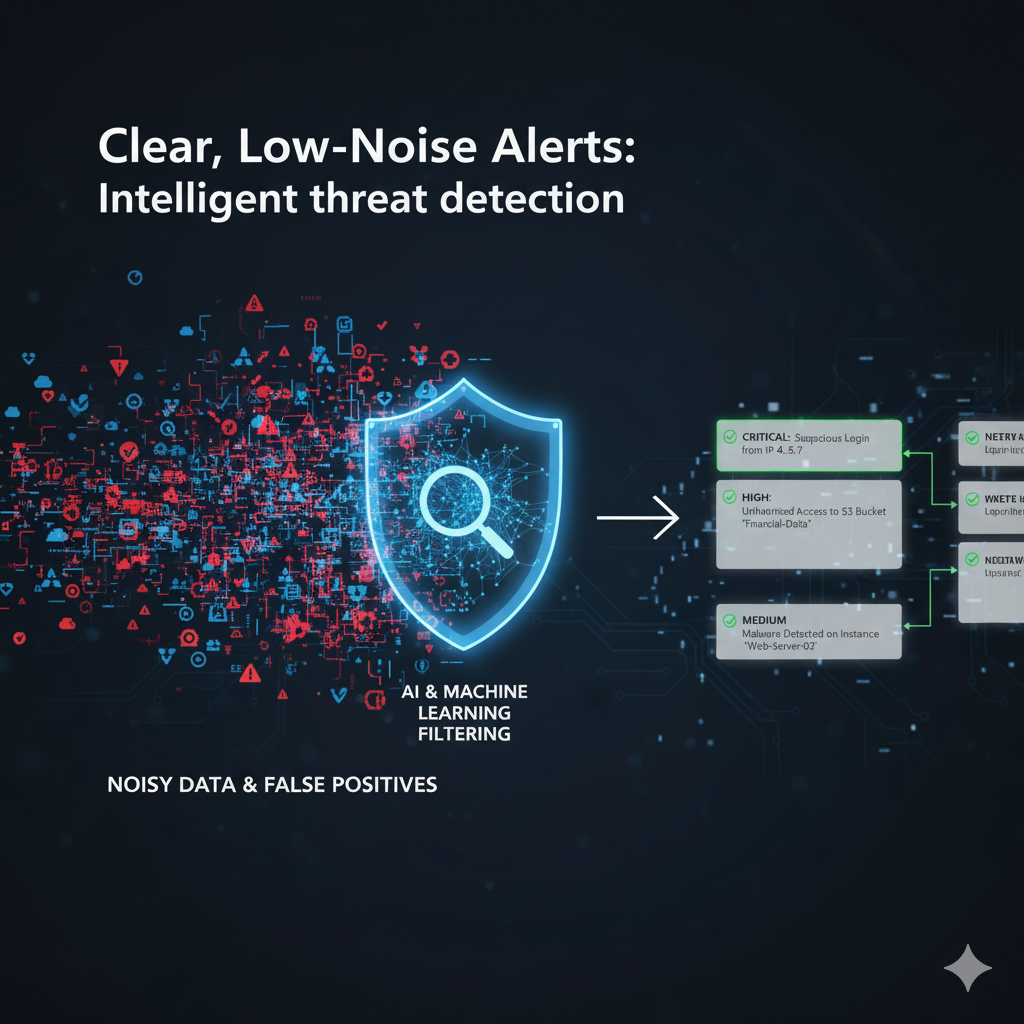
Session monitoring →
Get Started with Securitain